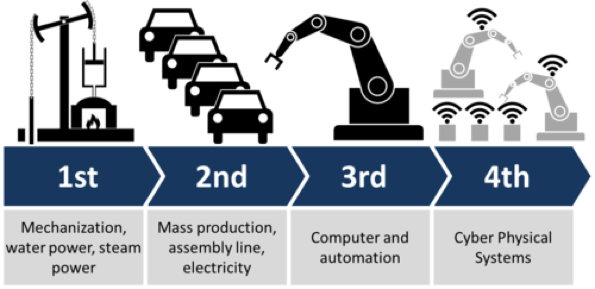
Since the concept was first articulated in 2011 by a German government-supported program promoting deeper integration of manufacturing software and hardware across the production value chain, the term “Industry 4.0” has gained recognition and momentum as the rallying cry for the 4th industrial revolution (see left Image by Christoph Roser at AllAboutLean.com). Wikipedia summarizes it like this: “Industry 4.0 facilitates the vision and execution of a ‘Smart Factory.’ Within the modular structured Smart Factories of Industry 4.0, cyber-physical systems monitor physical processes, create a virtual copy of the physical world, and make decentralized decisions. Over the Internet of Things, cyber-physical systems communicate and cooperate with each other and with humans in real-time…”
This definition may lead you to ask “What aspects of Industry 4.0 are truly revolutionary, and what technologies and tools are available today that would enable me to start building “Smart[er] Factories?” In this blog, I offer some potential answers to these questions that put the vision of Industry 4.0 within reach for automation practitioners familiar with the latest generation of SEMI Standards.
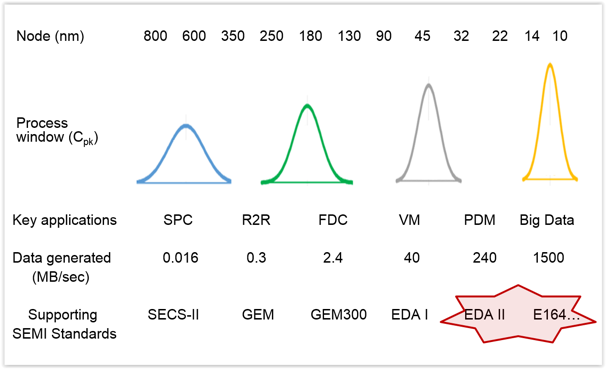
Semiconductor manufacturers have been collecting and using data from the equipment in their factories for decades. Throughout this period, device sizes and process windows have shrunk continuously according to Moore’s Law, and the SEMI Standards have evolved by necessity to support the insatiable demand for data exhibited by the process analysis and control applications that keep a modern fab running profitably (see left). The newest of these standards, the Equipment Data Acquisition suite (EDA, also known as “Interface A”), provides the power and flexibility to support a wide range of critical manufacturing applications and human users with ever-changing requirements; moreover, these standards can be deployed in a variety of system architectures without disturbing the “command and control” capabilities of existing factory systems.
“What does all this have to do with Industry 4.0?” To understand this, let’s look at the foundation of a “Smart Factory,” the collection of the many thousands of devices that might need to communicate over the so-called “Internet of Things.”
We already see evidence that the availability of low-cost, low-power, networkable computing hardware will likely result in an explosion of “smart sensors” and other intelligent devices on the factory floor. However, as social scientists have observed over the millennia, groups of smart individuals don’t necessarily exhibit smart behavior in the aggregate, so what additional attributes must these devices possess to be good citizens of a collaborative, Industry 4.0 environment? How will these devices communicate effectively with one another? And what oversight will be required to ensure this communication achieves the ultimate manufacturing objectives?
As a starting point, I propose that each device, or manufacturing “thing,” at a minimum should be discoverable, autonomous, model-based, self-aware, communicative, and well-behaved. Depending on the role the device must play, it might also be self-monitoring, capable of defending itself (secure), and a consumer of data from other devices/systems as well as a provider. So defined, these devices would need a minimum of external monitoring and supervision (read “management overhead”) to perform their basic functions, but would rely on higher-level systems to provide specific objectives, instructions, and constraints (read “configuration, recipes, and limits”) for their operation in a given context and timeframe.
I realize that’s a lot to absorb at once, but now imagine that each of these devices could implement a subset of the services called for in the EDA standards, especially those defined in E120/E125/E164 (equipment modeling and standard metadata modeling), E132 (session management), and E134 (data collection management). Consider the collaboration among independent devices and systems this would enable…and ask yourself, how much closer to the vision of Industry 4.0 can you possibly get?
I hope the ideas above were useful…or at least thought-provoking. We’ll be developing this theme further in the coming months, but I wanted to use this blog as a conversation starter. We’d love to hear your feedback, so give us a call, or feel free to reach out to us.♦




